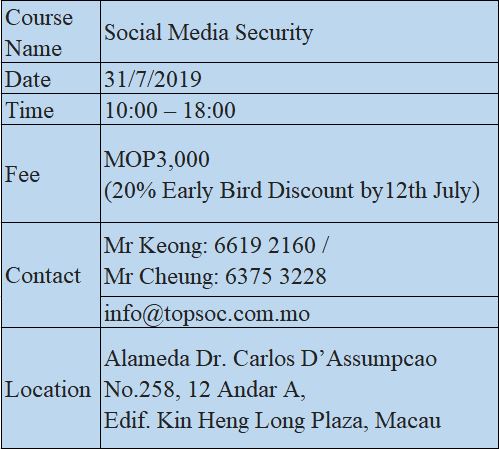
Course – Social Media Security
No one can totally escape from social media in nowadays society – WeChat, Facebook, Twitter, LinkedIn, Instagram… you named it. Social media is an excellent tool for enterprise in gathering and socializing with customers and its employees; it can be used in advertising, branding, or even collecting useful demographic information of clients. Social media sounds invincible, and yet, all good technologies are also double-edged swords: as convenient as it sounds, there is also risks and security concerns arising from the use of social media.
The aim of this one-day training is to equip participants with technological knowledge in social media, as well as to highlight the benefits and risks concerning the use of social media within the enterprise setting. Cases studies and lab session will also provide participants with practical knowledge on both deploying and exploiting social media tools.
Audience
Security Consultants/ Security Officers and Information Security Analysts/ IT Auditors/ Compliance Officers/IT Managers/ General Management/ Operation Management
Prerequisite
General awareness of information systems security.
Course Outline – Download Application Form and DetailsSocial Media 101
– What is social media
– Distinction of social media with other traditional media channel
– Social media as a strategic tool
– Keyword discovery and Google analytics
– Basic principle of Search Engine Optimization
– Social media adaptation – WeChat, Facebook, LinkedIn, Twitter, Google, Instagram, Weibo, Baidu Tieba (The time to be spent on the social media engine will be prioritized according to popularity)
Trends in Social Media
– Location Based Service
– Visual content in social media
– Enterprise collaborative system
– Gamification
Incidents and Issue on Social Media
– Famous bleaches of privacy and confidentiality using social media
– Social media impersonation
– Bot traffics
– Content farm and fake news
Social Media Security
– Social media security settings
– Social media monitoring
– Authentication and authorizations
– 3rd party applications and security
– Widgets, badges, plugins to web sites
– Passwords leakage
– Phishing and spamming
– Social Engineering
Lab Session
– Basic set up of social media tools
– Security settings for social media tools
– Google Analytics and Facebook Insights
– Social Media monitoring tools
– Click jacking
– Human Flesh Search
– Cross-site scripting & Cross-site request forgery
Instructor
Peter Cheung is the consultant of Hatter Company Limited.
Peter has over 15 years of experience in information technology and information security. Peter is a trainer on cloud security for a local entertainment company and trainer of Cloud security and threat course in HP. Peter also conducts security awareness training to various Hong Kong Government Department, insurance company and listed companies in Hong Kong.
Peter is a holder of CISSP from ISC2, CISA from ISACA and CCSK from Cloud Security Alliance (CSA). He is awarded an Information Security Leadership Achievements (ISLA) from ISC2 in 2013.